- The Booming Market for AI-Powered Cybersecurity
- AI’s Role in Improving App Security
- Real-World Impact: AI Shielding Mobile Users
- Integrating AI in Cybersecurity: Use Cases and Examples
- How to Weave AI into Your App Security Fabric
- Evolving AI-Powered App Security Risks and Their Countermeasures
- AI in App Security: Tools of the Trade
- The Price Tag: Cost to Implement AI in App Security
- Wrapping Up: The Intelligent Future of Mobile Security

Your mobile app is more than code; it's your frontline for customers’ trust and revenue. But with every new feature, the attack surface expands, leaving that trust—and your reputation—vulnerable. So, how do you innovate at speed without compromising security? The answer lies in enhancing mobile app security with AI.
Artificial Intelligence is stepping in as the essential co-pilot for modern defense. Forget sci-fi fantasies; we are witnessing a real-world shift where AI-powered mobile app security is becoming the new standard.
From detecting fraudulent transactions in real-time to identifying malware hidden in code, AI acts as a vigilant, automated guard.
To better understand how mobile app security with AI enables a more robust digital ecosystem, let’s start with a quick overview.
The Booming Market for AI-Powered Cybersecurity
The shift towards smarter, AI-driven security is not just a trend; it's a market reality backed by strong growth figures. The market data clearly indicates a surging global demand for intelligent security solutions.
- The AI in Cybersecurity market demonstrates explosive growth, valued at USD 25.40 billion in 2024 and forecasted to reach an astounding USD 219.53 billion by 2034, according to Polaris Market Research.
- Focusing specifically on the mobile application security segment, this market is projected to expand significantly from $10.91 billion in 2026 to $39.37 billion in 2034 at an impressive CAGR of 16.33%.
These robust figures highlight the increasing business commitment and reliance on leveraging AI-enhanced security to effectively protect mobile platforms and user trust.
AI’s Role in Improving App Security
Understanding AI's role in securing mobile applications is key to leveraging its power. It represents a significant shift from older security paradigms.
- AI app security fundamentally employs artificial intelligence and machine learning (ML) algorithms to actively predict, detect, prevent, and respond to cyber threats targeting them.
- This approach transforms mobile security from a reactive, signature-based system into an intelligent, adaptive defense capable of learning around the clock.
- Unlike traditional methods that wait for known threats, AI can identify novel threats by analyzing suspicious behavior, offering a crucial proactive advantage in a world where new mobile malware and attack strategies emerge daily.
Real-World Impact: AI Shielding Mobile Users
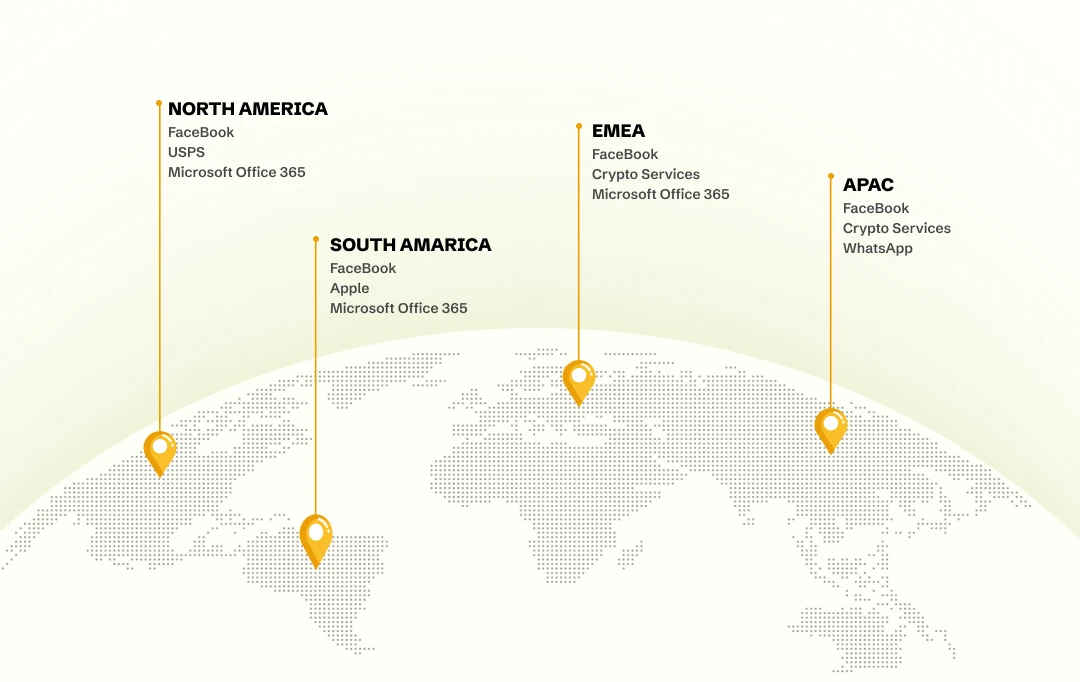
Zimperium’s 2026 Global Mobile Threat Report identified the top three brands in each region exploited for mishing (an attack that exploits mobile devices and apps) attacks in 2024. Facebook remained the constant name.
To stop such numbers from further growing, we are witnessing AI application security making a significant and positive difference across industries, protecting users and data more effectively than ever before.
- AI application security is demonstrably improving user protection in critical sectors such as finance and healthcare.
- For instance, many banking apps now widely use AI-driven systems for real-time fraud detection by analyzing transaction patterns and unusual user behaviors to flag anomalies.
- Similarly, integration of AI in healthcare, especially in mobile apps, is safeguarding sensitive patient data through vigilant monitoring of access patterns and the swift detection of unauthorized activities.
- A prominent example of AI's scalability and necessity in mobile security is Google's Play Protect service, which employs machine learning algorithms to scan billions of Android apps, thereby identifying and flagging potentially harmful applications. This continuous effort is vital for AI-powered malware detection in the expansive mobile ecosystem.
- Android’s open ecosystem, with sideloading and third-party app stores, increases malware risks, making AI’s real-time threat detection critical. To counter this, Android’s Play Protect scans 200 billion apps daily, leveraging AI to combat threats.
Integrating AI in Cybersecurity: Use Cases and Examples
AI's role in bolstering mobile app security is both diverse and profoundly impactful, functioning as a suite of intelligent capabilities that work together.
Its application in mobile app security extends beyond single solutions to encompass a range of coordinated intelligent functions, providing a comprehensive defense strategy.
Here’s how AI is making mobile apps safer:
| Use Cases | AI Applications & Examples | Key Benefits |
|---|---|---|
| Threat Detection | ML models analyze network traffic, app behavior, and code in real-time to identify malware, spyware, and phishing attempts, even zero-day exploits. | Proactive defense, reduced detection time |
| Behavioral Analysis | AI establishes baseline user behavior (e.g., login times, transaction types, data access) and flags anomalies that could indicate a compromised account. | Early fraud detection, personalized security |
| Vulnerability Management | AI tools scan app code (SAST/DAST) and identify potential weaknesses or insecure coding practices before deployment. | Fewer exploitable flaws, more secure development |
| Biometric Authentication | AI enhances facial recognition, fingerprint scanning, and voice ID by learning and adapting to subtle user changes, improving accuracy and spoof detection. | Stronger user authentication, reduced identity theft |
| Automated Response | AI can automatically block suspicious IPs, isolate affected app components, or trigger multi-factor authentication upon detecting a credible threat. | Faster incident response, minimized damage |
| Spam & Phishing Filtering | Natural Language Processing (NLP) analyzes messages and URLs within apps to detect and block phishing links or malicious content. | Protection against social engineering attacks |
| Data Loss Prevention (DLP) | AI monitors how data is used and transferred within the app, flagging or blocking unauthorized exfiltration attempts. | Enhanced protection of sensitive user data |
These application security benefits clearly demonstrate AI's capacity to create a more resilient and adaptive defense mechanism for the mobile applications we rely on daily.
How to Weave AI into Your App Security Fabric
Integrating AI in mobile app security isn't a plug-and-play affair, but a strategic process. It requires careful planning and meticulous execution for optimal results.
Here’s a roadmap to get you started:
1. Define Clear Security Objectives
What specific mobile threats are you most concerned about? Are you focused on fraud prevention, data leakage, or malware? Your goals will guide your AI strategy.
2. Data Collection and Preparation
High-quality, relevant data is the lifeblood of AI. You'll need to gather data on app usage patterns, network traffic, known threats, and user behavior. This data must be cleaned, labeled (if supervised learning is used), and anonymized to protect privacy.
3. Choose the Right AI Technologies/Models:
- Machine Learning (ML): For pattern recognition, anomaly detection, and predictive analytics (e.g., Random Forest, SVMs, Neural Networks).
- Deep Learning (DL): A subset of ML, excellent for complex tasks like image recognition in biometrics or analyzing sophisticated malware.
- Natural Language Processing (NLP): From understanding and analyzing text-based data to detecting phishing attempts or malicious commands, NLP use cases can be diverse.
4. Develop or Select AI Models
You can develop custom AI models or leverage pre-trained models and AI security platforms from specialized vendors. Consider the complexity, cost, and expertise required.
5. Integration with Security Infrastructure
AI tools need to be integrated into your existing security workflows and mobile app development lifecycle (DevSecOps). This often involves APIs and security information and event management (SIEM) systems.
6. Rigorous Testing
Your end-to-end testing strategy should leverage AI systems extensively. This includes identifying factors like:
- Accuracy and Efficacy: Does it correctly identify threats? What’s the rate of false positives and false negatives?
- Performance: How does it impact app performance and user experience? Mobile AI security should be efficient.
- Adversarial Testing: Attempt to deceive the AI models to understand and mitigate potential evasion techniques.
7. Deployment and Continuous Monitoring
Once deployed, AI security systems require ongoing monitoring. Threat landscapes evolve, so AI models must be regularly retrained and updated with new data to maintain their effectiveness. This is a key aspect of the latest mobile security trends.
8. Compliance and Ethics
Ensure your mobile app security practices comply with data privacy regulations (like GDPR, CCPA) and Ethical AI guidelines, particularly regarding user data handling and potential biases in algorithms.
9. Platform-Specific Integration
Tailor AI models to platform requirements. For iOS, use on-device ML frameworks like Core ML to comply with Apple’s privacy rules. For Android, leverage Google’s ML Kit for scalable threat detection. Test compatibility with platform-specific APIs.
10. User Communication
Transparently inform users about AI-driven security measures (e.g., via app notifications) to build trust, as 75% of users probably won’t make a purchase if they don’t trust the company with the data.
Evolving AI-Powered App Security Risks and Their Countermeasures
On one hand, folks are using AI to defend their solutions from cyberattacks, on the other hand, AI is leveraged to cause these attacks. Here are some of these attacks you, as a developer, will often come across.
Use these countermeasures to keep yourself ready!
| AI Security Risks | Descriptions | Countermeasures |
|---|---|---|
| Model Theft | Attackers steal proprietary AI models through unauthorized API access or reverse-engineering. | Secure APIs with strong authentication; encrypt models and monitor for unusual access. |
| Insecure Plugin Design | Flawed plugins allow malicious code execution or unauthorized data access. | Restrict plugin permissions; isolate execution environments and audit code. |
| Adversarial Attacks | Malicious inputs exploit model weaknesses, causing misclassification or incorrect outputs. | Use adversarial training; implement robust input validation and anomaly detection. |
| Training Data Poisoning | Corrupted training data manipulates model behavior to produce harmful results. | Vet data sources; apply strict filtering and sandboxing during data collection. |
| Overreliance | Excessive trust in AI outputs leads to undetected errors or security oversights. | Require human review for critical decisions; validate outputs against reliable sources. |
| Data Leakage via Embeddings | Sensitive data embedded in model outputs or embeddings is extracted by attackers. | Use differential privacy; sanitize embeddings and limit output granularity. |
| Prompt Injection | Crafted inputs trick AI into executing harmful actions or revealing sensitive data. | Sanitize inputs; limit model permissions and use context-aware filtering. |
| Model Denial of Service | Attackers overload AI with complex queries, disrupting app performance. | Apply rate limiting and input size restrictions; monitor resource usage. |
| Sensitive Information Disclosure | AI unintentionally exposes private data from training sets or user interactions. | Encrypt sensitive data; use federated learning and provide user opt-out controls. |
| Model Inversion | Attackers reconstruct training data by analyzing model outputs or gradients. | Apply differential privacy; limit output detail and use secure aggregation. |
| Supply Chain Vulnerabilities | Compromised third-party components introduce security flaws into AI systems. | Scan libraries and APIs; use trusted vendors and maintain a component allowlist. |
| Jailbreaking | Attackers bypass AI safety restrictions to access unauthorized functionality. | Implement robust guardrails; regularly test and update model constraints. |
| Excessive Agency | Overly autonomous AI performs unintended actions, risking security or compliance. | Restrict AI decision-making scope; enforce human oversight for sensitive tasks. |
| Insecure Output Handling | Unfiltered AI outputs enable attacks like XSS or malicious code execution. | Validate and sanitize outputs; block direct execution of untrusted responses. |
AI in App Security: Tools of the Trade
The marketplace is responding to the need for smarter security with an increasing variety of AI-powered tools. These tools vary widely, ranging from broad, all-encompassing platforms that offer a suite of security features to highly specialized solutions targeting niche security concerns.
Here are some notable examples (while specific "mobile-only" AI security tools are emerging, many leading AppSec and endpoint security tools incorporate AI that benefits mobile environments):
| Tools | Key AI-Powered Features for App Security |
|---|---|
| NowSecure Platform | Offers automated mobile app security testing, identifies AI-related risks such as leaked API keys, and performs OWASP MASVS compliance testing |
| Zimperium’s z Platform | Includes on-device, real-time threat detection for mobile devices and apps, along with an AI-powered engine to detect known/unknown threats |
| Darktrace | Enterprise-wide cyber AI that detects and responds to threats in real-time, including those affecting mobile endpoints |
| CrowdStrike Falcon | A cloud-native endpoint protection platform that leverages AI for next-gen antivirus, threat hunting, and enhanced mobile device security |
| Microsoft Defender for Endpoint | Includes mobile threat defense capabilities, leveraging Microsoft's AI and ML for threat detection and response |
| DataTheorem | Mobile application security (MAS) analyzer for API and mobile app discovery, inspection, and protection using AI |
When selecting tools, it's wise to consider factors like ease of integration, scalability, the specific types of threats detected, and comprehensive support for your target mobile platforms. Engaging with specialized mobile app development companies that possess deep expertise in security can also provide invaluable insights and guidance.
The Price Tag: Cost to Implement AI in App Security
Understanding the financial commitment is crucial when planning to integrate AI into your mobile security strategy.
Integrating AI in mobile app security involves costs that can fluctuate considerably based on project scope and complexity, which means there's no standard price tag.
Here’s a little bit about some crucial factors influencing the budget.
1. AI Model Complexity & Development
Custom AI models designed for security can range from $50,000 to over $500,000, largely depending on their sophistication and the problems they solve.
2. Data Acquisition & Preparation
The process of gathering, cleaning, and labeling the specialized datasets required for training AI security models may cost between $5,000 and $50,000 or more.
3. Talent Acquisition
Hiring skilled professionals with expertise in AI in cybersecurity presents a significant ongoing cost due to high salary demands in these specialized fields.
4. Infrastructure Requirements
Utilizing cloud computing resources for AI model training and operational deployment (e.g., AWS, Azure, GCP) can incur monthly costs from $1,000 to potentially over $100,000 for very large-scale security operations.
5. Integration & Deployment
Successfully connecting AI tools with your existing application infrastructure and established security systems requires dedicated time, resources, and expertise.
6. Third-Party Tools & Platforms
Licensing fees for commercial AI security software or specialized platforms will constitute recurring operational expenses.
7. Ongoing Maintenance & Updates:
AI models necessitate continuous monitoring, periodic retraining with new data, and updates, typically adding 15-25% of the initial app development cost annually. This additional cost is often planned under app maintenance budgets by expert developers.
8. Security & Compliance Adherence
Ensuring that the AI solution itself is secure and fully compliant with pertinent data regulations can add an additional $10,000 to $100,000+ to the budget.
It is vital for decision-makers to weigh these substantial upfront and ongoing costs against the potentially devastating financial and reputational expenses associated with a major security breach.
Wrapping Up: The Intelligent Future of Mobile Security
In today's mobile landscape, AI is no longer just a security feature—it's a core business strategy. The proof is in the capital: with the AI in the Cybersecurity market projected to surge towards $220 billion by 2034, it is clear where industry leaders are placing their bets to survive.
This massive investment is driven by AI's unique power to transform security from a reactive chore into a proactive hunt, analyzing behavior and neutralizing threats before they can strike.
However, this power is a double-edged sword, as adversaries now use AI to architect smarter, more evasive attacks. The winning strategy, therefore, is not just about adopting AI, but mastering it with vigilance against new risks like model theft and data poisoning.
In the relentless battle for digital trust, where 64% of users are already deeply concerned about data privacy, your investment in intelligent security is the only firewall that truly matters.
Frequently Asked Questions
-
Can AI replace cybersecurity?
-
How is AI a threat to app security?
-
What is the best AI for app security?
-
How can AI be used in app security?
-
What app security systems use AI?
-
How to use AI in network security?