As an app developer, you want to make sure that the app you are building is flawless and secure from all the unethical attacks at the same time. And in order to make your mobile application secure from such cyber attacks, the app developers are required to follow certain security practices and strategies.
In the case of mobile app development, the symmetric encryption with AES in Java and Android can turn out to be one of the best security practices. So if you have questions regarding common block modes, data protection from modification, the need for initialization vectors etc. this article might be of great help to you.
But before we jump straight to the security strategy execution part, let's take a look at the AES and be aware of the basic understanding behind the concept.
What does AES stand for?
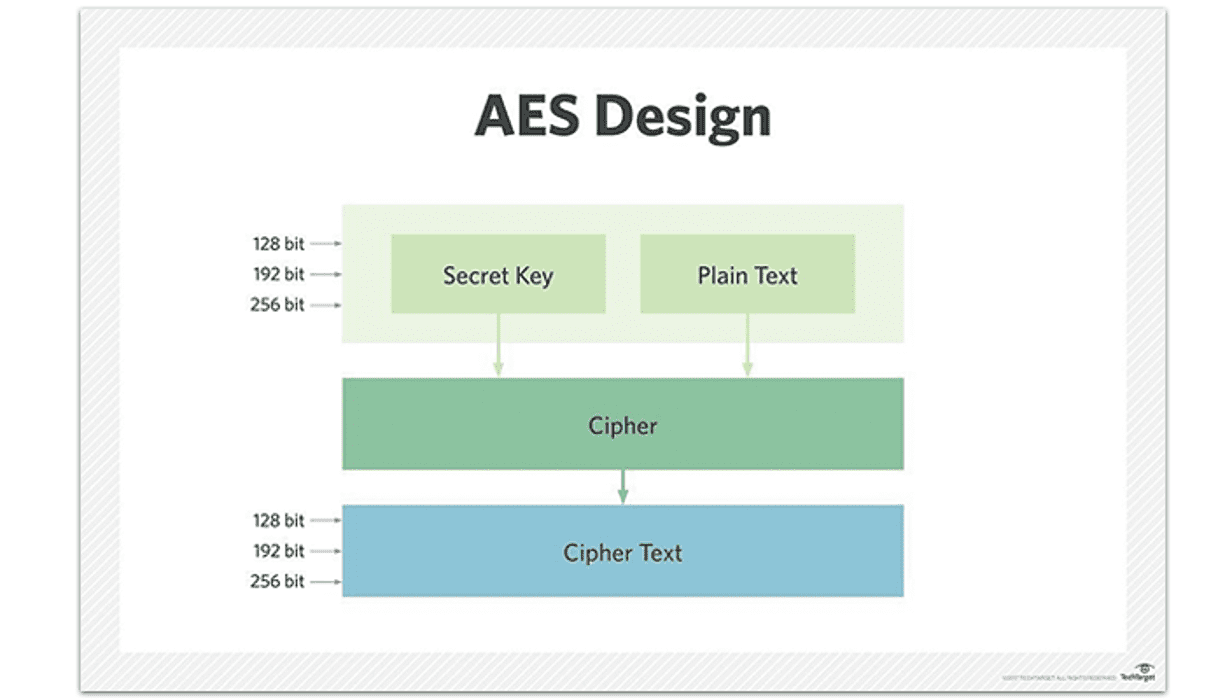
The term AES stands for Advanced Encryption Standard, which can be defined as a symmetric block cipher that has been chosen by the government of the U.S. This was done to protect classified information and is also being currently applied in the hardware and software industries all over the globe.
AES is also known by its original name 'Rijndael' which was first elected by the NIST in the year 2000 as a successor to the traditional DES i.e. Data Encryption Standard.
As a block cipher, it performs encryption with fixed-length groups of bits. For instance, the algorithm defines 128-bit blocks mainly, but the Advanced Encryption Standard also supports key lengths of 192-bit and 256-bit as well.
During this process, each and every block has to go through a number of cycles that are transformation rounds. Here, one thing that needs to be remembered is that the block size is not affected by the length of the key except for the total number of repetitions. For example, the 128-bit has 10 cycles whereas the 256-bit has 14 cycles.
How to Encrypt the Blocks?
Let's consider a situation where the Java and Android app developers want to encrypt entire messages instead of just the information that is in 128-bit. In order to perform this procedure, you need to pick a block mode that provides the support of multiple blocks which can be further encrypted into a particular ciphertext format.
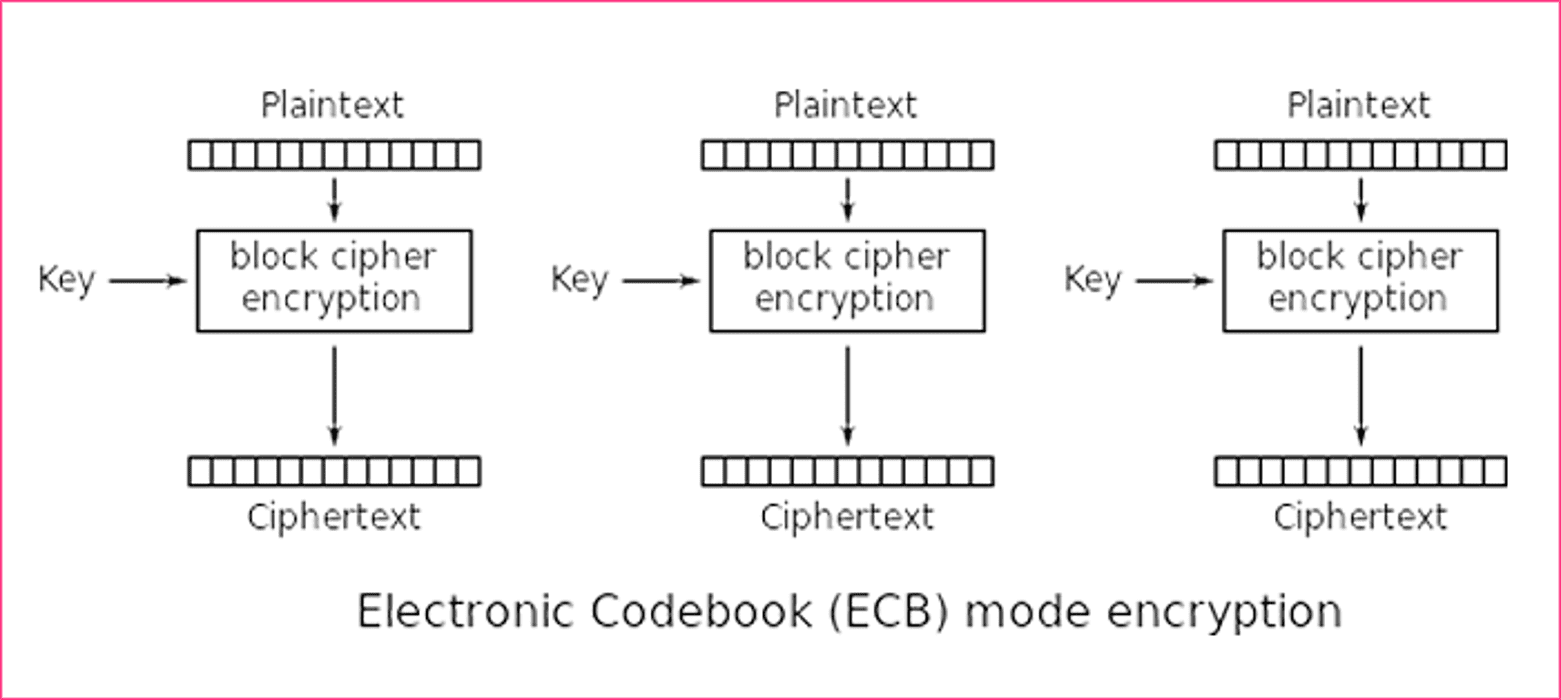
One of the simplest block modes is ECB which stands for Electronic Codebook which uses the same unaltered key on every single block, as shown in the above image. But this method is not that effective at working because identical plain text blocks are being encrypted into identical ciphertext blocks.
We only recommend using this block mode for encrypting if your data is smaller than the 128-bit. But if the size of your data is bigger than 128-bit then padding is required to make the encryption effective. In other words, padding is the filling of the missing bits of blocks with zeros.
CTR vs CBC
1. Counter Mode (CTR)
The block mode of CTR which is also known as ‘Counter Mode’ is comparatively complex to understand but it is highly efficient. In block mode, the block cipher is transformed into a stream cipher, which doesn't require any padding for proper functioning. If we look in the basic form, every block is provided with a number from 0 to n.
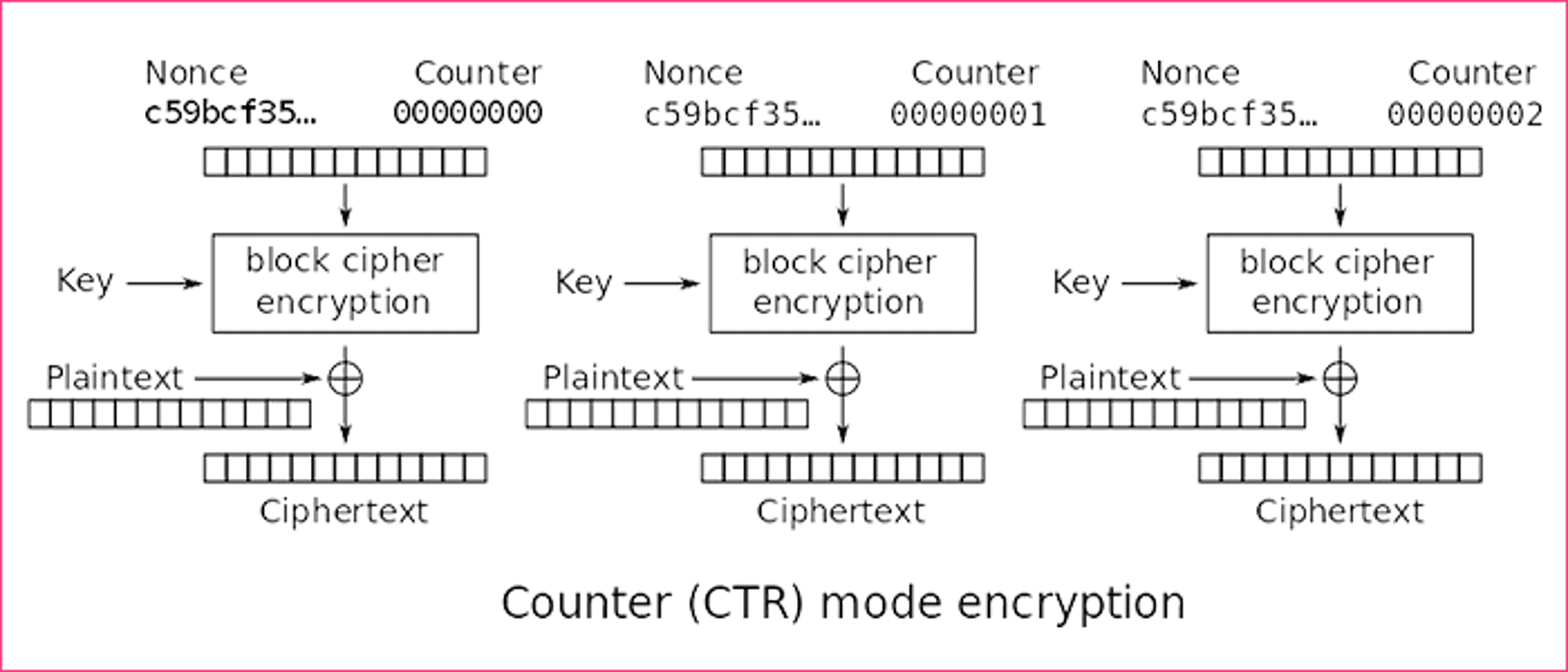
Every block will now be encrypted with the key, the IV (also called nonce here) and the counter value. Now, all the blocks will be encrypted with the key, counter value and even the nonce. CTR has one advantage over CBC, in Counter Mode, the encryption can be done in parallel where every block is dependent on the nonce.
2. Cipher Block Chaining (CBC)
In the case of CBC i.e. Cipher Block Chaining, XORs are involved with the plain text blocks and the ciphertext blocks that have been previously used. With these methods, all ciphertext blocks become dependent on every plain text block that is being processed during the encryption process.
When it comes to transmitting data, the Java and Android app developers can directly relate nonce to the real cipher message. But the easiest way to encrypt is by using a block that is filled with zeros. This will lead to the same ciphertext as the same key being encrypted again and again.

The above image showcases the example of the encryption process in the Cipher Block Chaining (CBC) method. The result is indistinguishable from a lot of noise combined with random data. Apart from this, it is important that the nonce is public as well as random in context to be used only once.
Implementation of AES in Java and Android
In the modern day, Java offers us all the tools we need, but when it comes to the part of crypto API, the process can become complicated. The responsibility of an application developer includes assuring the parameters like length and size that are to be used in the process.
Here is an example of a 128-bit key that is generated on random. At this point, the appropriate mode will be chosen by Java automatically whenever a key passes with 192-bit and 256-bit length.
SecureRandom secureRandom = new SecureRandom();
byte[] key = new byte[16];
secureRandom.nextBytes(key);
SecretKey secretKey = SecretKeySpec(key, “AES”);
The next step is to create initialization vector with GCM, a random byte-array of 12 bytes instead of 16 to make it more fast and secure.
byte[] iv = new byte[12]; //NEVER REUSE THIS IV WITH SAME KEY
secureRandom.nextBytes(iv);
After that is done, initialize your cipher in the mode AES-GCM which is easily available for a majority of Android, Java and modern JREs.
final Cipher cipher = Cipher.getInstance("AES/GCM/NoPadding");
GCMParameterSpec parameterSpec = new GCMParameterSpec(128, iv); //128 bit auth tag length
cipher.init(Cipher.ENCRYPT_MODE, secretKey, parameterSpec);
Finally, the app developers can concat the entire information discussed in the previous steps into a single message.
ByteBuffer byteBuffer = ByteBuffer.allocate(4 + iv.length + cipherText.length);
byteBuffer.putInt(iv.length);
byteBuffer.put(iv);
byteBuffer.put(cipherText);
byte[] cipherMessage = byteBuffer.array();
So, these were the steps required for the symmetric encryption to take place in Java and Android. The encrypted data, as well as the authentication tag, are then adjoined into a single byte array.
Conclusion
The question that arises with the symmetric encryption is, 'Are the messages completely secure?' And in reality, we can state that encryption does not automatically protect your information against data modification. This is the reason why it is quite a common attack.

To completely secure your data, the developers have the option to include additional elements to it. For example, the MAC or Message Authentication Code can be added as a digital signature to the message being encrypted. You can even use this Message Authentication Code for authentication and verification purposes.
In case you would like to know more about the different processes of data encryption and what role it plays in the mobile app industry, just make sure you click on that ‘Subscribe’ button.















